Why Businesses Should Care About Ransomware
In the past couple of years, there has been a proliferation of ransomware attacks affecting individuals and organizations, ranging from government institutions to corporations, and small businesses.
It’s a fairly popular attack tactic among hackers, mostly because of its sheer capability to easily extort from victims.
But, what exactly are we talking about here?
What is Ransomware?
Imagine walking into your office one morning to find all your workstations padlocked, with a guy demanding hundreds of dollars to unlock them.
That’s exactly how ransomware works. It’s a particular type of virus that encrypts files on a computer or smartphone, and subsequently, demands a ransom to decrypt data and restore your files.
Prevalence of Attacks
Ransomware continues to grow at an alarming rate.
Home and business computers in the United States have got hit with an average of 4,000 ransomware attacks each day this year – that’s a 300% increase over 2015, according to the U.S. Department of Justice.
And according to data released by the FBI, more than $24 million was lost by victims due to such attacks in 2015 alone. This year, ransomware victims paid an estimated $209 million in just the first three months of this year.
Protecting Your Business From Ransomware
#1. Backup Your Data
Data backup is undoubtedly one of the most effective strategies against ransomware attacks.
It may not prevent an attack, but it will allow you to recover files and restore operations without paying a ransom.

Typically, there are two options for backing up your data, and they are an external drive or the cloud.
Unfortunately, ransomware viruses, like the all-too-common Cryptolocker, can attack your drives and encrypt even primary local backups attached to your network.
That leaves many small premises looking for secure, off-premise backup. Of course, security is a significant concern for businesses thinking about transferring data offsite, to the cloud.
That’s why you need to pick an online backup service that offers encryption of your business data, before it gets sent to the cloud, at rest, and in flight.
Take Carbonite, for example. When installing Carbonite’s cloud backup software, business owners have the chance to pick their security passphrase; that will not get transferred over the Internet.
Instead, it remains 100% in control of the business. Carbonite encrypts files locally with a sophisticated 128-bit Blowfish encryption algorithm.
#2. Simplicity is Key
As a business, you certainly have more things to worry about than data backup. But data backup is necessary, especially with the recent uptick in ransomware attacks.
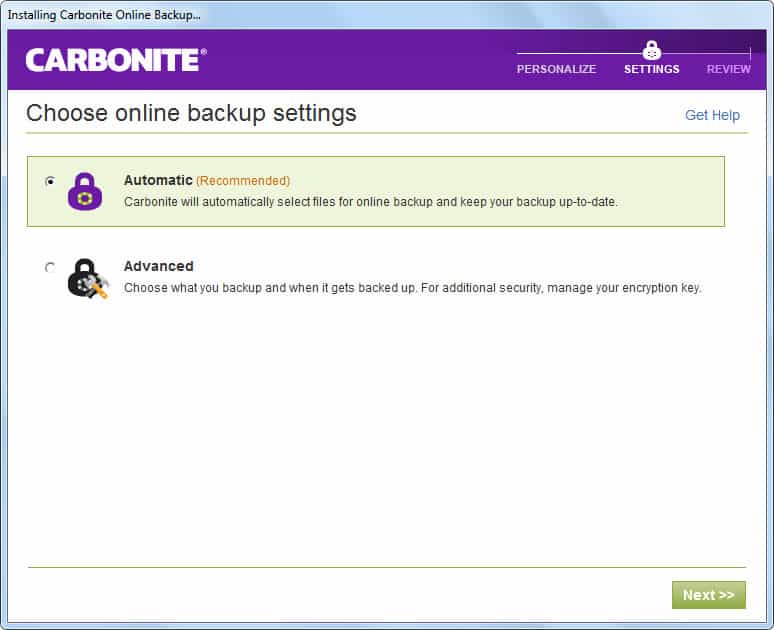
However, it should never get in the way of your day-to-day operations. Excellent cloud backup services, offer users an easy step-by-step wizard, that will guide them through each step of the backup process.
Here is an example of Carbonite’s setup wizard:
If you’re thinking about protecting a business from the ransomware epidemic, data backup should be your first bet.
Cloud data backup adds security layers, because business files are stored off-site, and therefore are protected from:
- Fires
- Floods
- Human error
#3. Rely On a Layered Security Framework
Cloud backup can help you comfortably recover lost files and reduce downtime.

You still need a robust security framework to protect from emerging ransomware. In addition to firewalls, a layered security framework should encompass web filtering and antiviruses.
Across the system network and within all endpoint devices. A layered security framework substantially minimizes the chances of any ransomware gaining access to your business environment.
#4. Update Security Strategies
As security technologies continue evolving, hackers are gradually reviewing and improving their strategies as well, to keep up with the latest advancements.
Therefore, software that may be effective against Cryptolocker today may become useless against other types of ransomware, in a couple of months’ time.
Consider a May 2016 report by Duo Security, that revealed, a majority of endpoint device users are running gadgets on vulnerable and outdated software versions.
Tweet This
Only 35% of Windows users have upgraded to Windows 8.1 or 10, and 53% of Mac OS users are on the latest version.
This fact alone gives hackers the upper hand in attacking and gaining full system access through any of these endpoint devices.
With that in mind, it’s essential to ensure that all your security layers are up-to-date, and that includes every single software patch released.
#5. Manage System Privileges
According to a 2015 survey by Lumension and Ponemon Institute, 75% of malware gain access to systems through endpoint devices.

The level of system damage by malware is dependent on the particular privileges of the compromised endpoint device.
If a compromised device has global administrative privileges, for instance, ransomware could gain complete system control, and subsequently, cripple organizations operations.
In addition to updating security systems and software across your company’s devices, you should keenly monitor and manage all system privileges via various access points.
Only the most secure devices should have administrative privileges.
In Summary…
Finally, it’s advisable to consult a reputable professional to periodically review your entire system framework.
And implement requisite measures against ransomware, according to your respective vulnerabilities. Thanks for sticking around till the end, and please don’t forget to leave your comments and thoughts below.